Intro
System calls are an essential part of operating systems, acting as the bridge between user applications and the kernel. They allow user programs to request services from the kernel, such as reading from or writing to files, creating processes, and communicating with hardware. This blog aims to provide a thorough understanding of system calls, their significance, and how they operate within an operating system.
Video Index
- Understanding Kernel Mode and User Mode
- Understanding System Calls
- Working With System Calls
Step 1: Understanding Kernel Mode and User Mode
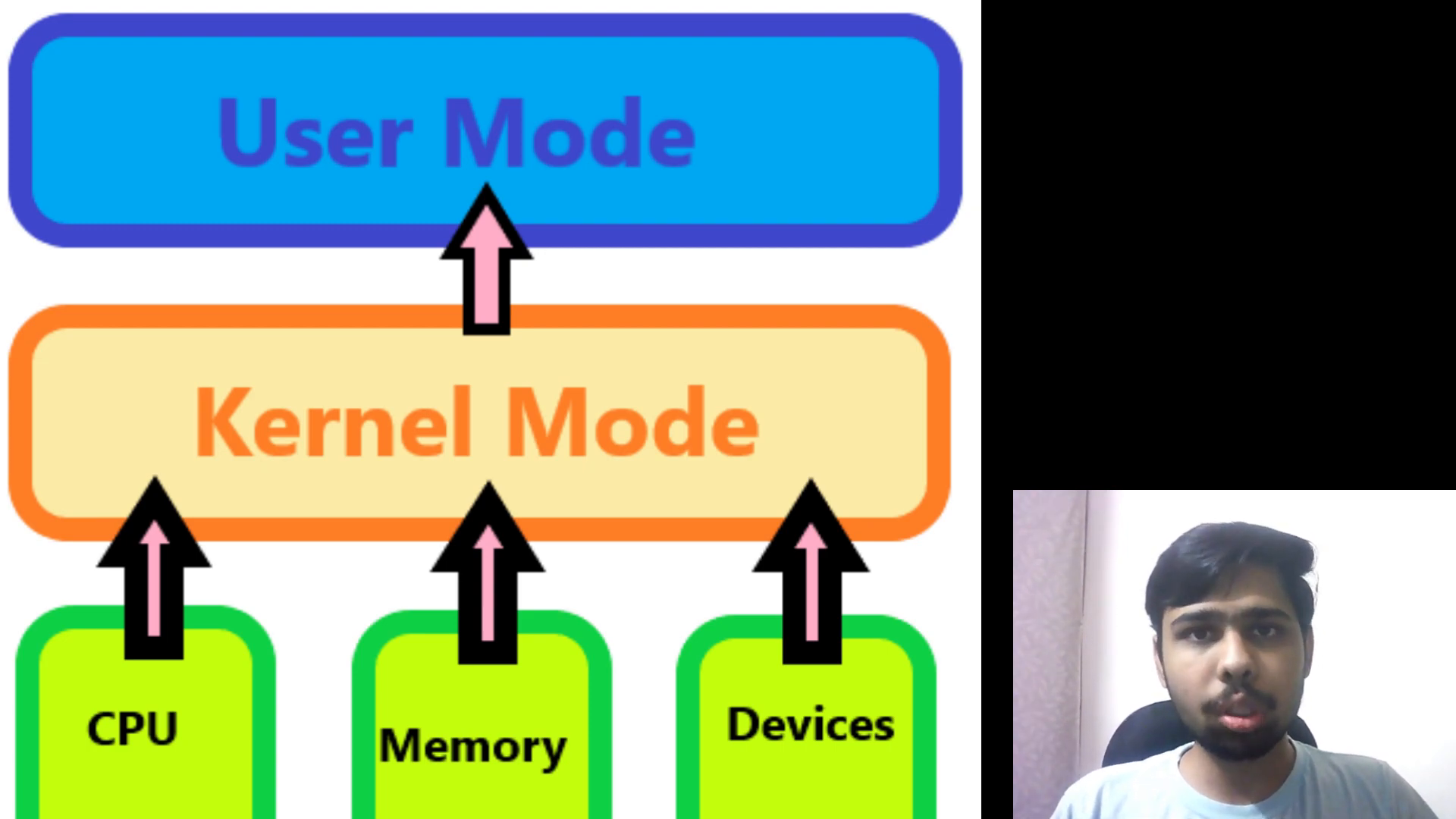
To grasp the concept of system calls, we first need to understand the two primary modes of operation in an operating system: Kernel Mode and User Mode.
What is Kernel Mode?
Kernel mode is a privileged mode where the operating system has full access to all hardware and can execute any CPU instruction. In this mode, the kernel can manage system resources, access memory directly, and control hardware devices. This mode is essential for performing critical tasks that require direct interaction with the hardware.
What is User Mode?
User mode, on the other hand, is a restricted mode where user applications run with limited access to system resources. Applications in user mode cannot directly access hardware or memory locations that belong to the kernel. Instead, they must use system calls to request services from the kernel, ensuring that the system remains stable and secure.
Why Are These Modes Important?
The separation of user mode and kernel mode is crucial for system security and stability. It helps prevent user applications from interfering with the kernel or other applications, which could lead to system crashes or security breaches. By controlling access to hardware and memory, the operating system can maintain a stable environment for all running applications.
Step 2: Understanding System Calls
System calls serve as the interface between user applications and the kernel, enabling users to perform operations that require higher privileges. When a user program needs to perform a task such as reading a file or allocating memory, it makes a system call to request the kernel's assistance.
How Do System Calls Work?
When a system call is invoked, the following steps typically occur:
- The user application prepares the necessary parameters for the system call.
- The application triggers a software interrupt to switch from user mode to kernel mode.
- The kernel examines the parameters and executes the requested operation.
- The kernel returns the results to the user application and switches back to user mode.
Types of System Calls
System calls can be categorized into several types based on their functionality:
- File Management: Creating, opening, reading, writing, and deleting files.
- Process Control: Creating, terminating, and managing processes.
- Device Management: Interacting with hardware devices.
- Information Maintenance: Getting and setting system information.
- Communication: Facilitating communication between processes.
Step 3: Working With System Calls
Now that we understand what system calls are and how they function, let's explore how to use them in programming.
Making a System Call
To make a system call in a program, you typically follow these steps:
- Include the necessary header files that define the system calls.
- Prepare the arguments that the system call requires.
- Invoke the system call using the appropriate function.
Example of a Simple System Call
Let's consider an example where we want to write "Hello, World!" to the standard output. Here’s how you can do it in C:
#include <unistd.h>
int main() {
const char *message = "Hello, World!\n";
write(1, message, 13); // 1 is the file descriptor for stdout
return 0;
}
In this example, the `write` function is a system call that takes three arguments:
- The file descriptor (1 for standard output).
- A pointer to the buffer containing the data to be written.
- The number of bytes to write (13 in this case).
Handling Errors in System Calls
When working with system calls, it’s crucial to handle potential errors. Most system calls will return a negative value to indicate an error. You can use the errno variable to determine the specific error that occurred. Here’s a modified version of our previous example that includes error handling:
#include <unistd.h>
#include <stdio.h>
#include <string.h>
#include <errno.h>
int main() {
const char *message = "Hello, World!\n";
if (write(1, message, 13) < 0) {
perror("write failed");
}
return 0;
}
In this code, if the `write` call fails, the program will print an error message describing the failure.
Exploring System Call Interfaces
To see all available system calls on your system, you can check the relevant header files. For example, in a Linux environment, you can find system calls in the /usr/include/unistd.h file. You will find a list of functions that correspond to various system calls, which you can use in your applications.
Conclusion
Understanding system calls is essential for anyone interested in operating systems, programming, or reverse engineering. They provide the necessary interface for user applications to request services from the kernel, ensuring that the system operates smoothly and securely. By mastering system calls, you can gain deeper insights into how operating systems function and enhance your programming skills.
Comments
Post a Comment